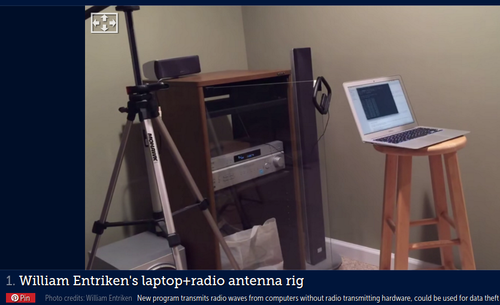
There is reportedly a new particularly advanced USB-savvy malware being called "USB Thief" (Google Search) being discussed by many in the technology press.
If you allow users (including system admins) to use USB storage devices on air gapped systems then this threat can be a potential attack vector a persistent attacker could deploy against your organization.
Basically an infected USB device could be inserted into an air gapped computer where it could collect considerable amount of "protected data" and then exfiltrate the "protected data" back to the infected USB device. Once the device is removed there is reportedly no trace of the malware on the compromised system and no record of the data collected.
Best defense would be not to allow USB storage media on air gapped systems. Otherwise, restricting data migration from the air gapped network (i.e. the high-side) to the internet network (i.e. the low-side) would be another defensive measure. Good physical security would also limit the effectiveness of this threat vector.
Some links with more coverage (some of it F.U.D.): techtimes.com, sci24h.com, arstechnica.com, pcworld.com, thestack.com, securitybrief.co.nz, slashdot.org, idgconnect.com, and itsecuritynews.info,